How Uber Payment System Handles 30 Million Transactions Per Day
#114: Payment System Design - Part 1
Share this post & I'll send you some rewards for the referrals.
Block diagrams created using Eraser.
I launched Design, Build, Scale to elevate your software engineering career…
Here’s what you’ll get inside:
High-level architecture of real-world systems.
Deep dive into how popular real-world systems actually work.
How real-world systems handle scale, reliability, and performance.
And here’s the best part:
You’ll get 10x the results you currently get with 1/10 the time, energy & effort.
Onward.
What happens when you throw 10,000 agents at a research question? (Partner)
We asked this question, then built the backend infrastructure to find out.
Most research tools are designed for a human to read the output. You ask a question; you get an essay. That works fine when someone is sitting at a screen. But if you’re building systems where another machine consumes the research (compliance pipelines, knowledge graphs, decision engines), your entire architecture and philosophy change.
AgentField is the control plane for building large-scale AI-Backends that make this possible.
Here’s the interesting part. You don’t just parallelize the work. The agents coordinate:
They identify gaps in collective findings and spawn sub-questions to fill them
Parallel streams cross-reference each other to catch contradictions
Higher-order synthesis surfaces patterns across sources that no single document reveals
The coordination problem alone is nontrivial.
Thousands of agents need to avoid duplicate work, share relevant context, and collectively converge on completeness. We borrowed patterns from distributed consensus and applied them to autonomous research workloads.
The largest deployment we’ve tested: 100,000 agents running simultaneously. 🚀
It’s open source under Apache 2.0 and works with any LLM (Claude, Ollama, DeepSeek).
Learn and build the Deep Research example: https://github.com/Agent-Field/agentfield
⭐ Star the repo if you’re building AI backends.
October 2014 - Prague, Czech Republic.
Maria has an important meeting in 15 minutes.
But she doesn’t have cash for a taxi.
So she opens the ride-sharing app called Uber & requests a ride.
Although it’s stunning how easily Uber processes payments, handling payments at ‘scale’ is extremely HARD.
Here are some problems:
1. Security
A user adds payment details on the mobile app.
Yet a mobile device could get stolen, or Uber servers could get breached…
So it’s highly risky to store sensitive information on mobile devices & Uber servers.
2. Disbursement
A single payment has to be split across different trip participants:
Driver
Uber platform
Tax, fees, and so on
i.e., money cannot simply move directly from rider to driver.
3. Reliability
Payments include “external systems” such as banks, card networks, and payment providers.
But there’s a risk of network failures, timeouts, and partial outages.
And this could create a dreadful user experience.
Payment System Design
Here’s how Uber payment architecture works:
1. Add Payment Information
A user adds payment details, such as credit card number & CVV, to the mobile app.
Yet it’s RISKY for them to store this data because:
It’s hard to secure
It requires heavy legal compliance
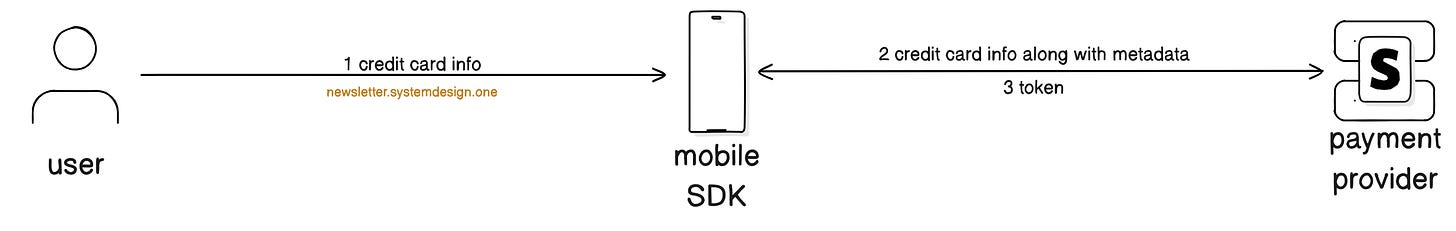
So they use payment provider1 SDK2 in the mobile app to collect sensitive details.
Software development kit (SDK) doesn’t send card information to Uber servers.
Instead, it “securely” collects credit card information and sends it directly to the payment provider, along with contextual metadata. Metadata includes Uber account details, payment method type (card or wallet), and so on.
Payment provider then returns a unique token,,, which acts as a ‘safe reference’ for the credit card. The token represents the card; think of it as a (reusable) permission to charge the card.
Plus, the payment provider binds the received metadata to the token to scope its usage and validation.
From this point on, mobile app uses the token instead of the credit card.
i.e., Uber or mobile device has NO sensitive data.
IMPORTANT NOTE:
A stolen token is useless because it’s created by the payment provider, tied to Uber’s account and app, and restricted to specific uses (such as charges made only by Uber). So another mobile device or app cannot use it to charge the card.
Ready for the best part?
Reminder: this is a teaser of the subscriber-only newsletter series, exclusive to my golden members.
When you upgrade, you’ll get:
High-level architecture of real-world systems.
Deep dive into how popular real-world systems actually work.
How real-world systems handle scale, reliability, and performance.