Everything You Need to Know About Cache Strategies ⭐
#74: A Simple Introduction to Cache Strategies (3 Minutes)
Get my system design playbook for FREE on newsletter signup:
This post outlines popular cache strategies. You will find references at the bottom of this page if you want to go deeper.
Share this post & I'll send you some rewards for the referrals.
Once upon a time, there lived a junior software engineer named Asahi.
He worked for a tech company named Hooli.
Although smart, he never received the opportunity to work on any interesting project.
So he was sad and frustrated.
Until one day, when he had the idea of applying for a new job.
And the interviewer asked him 1 simple question,
“Can you list 5 popular cache strategies?”.
Yet he failed to answer it, and the interview was over in 7 minutes.
So he studied it later to fill the knowledge gap.
Onward.
Shape the future of AI with Outlier—Sponsor
Outlier is hiring experienced developers to help train cutting-edge AI models with expert human feedback. Work flexibly from anywhere, get paid weekly (up to $50/hr), and apply your real-world dev skills to real AI challenges—no AI experience required.
Cache Strategies
He failed the interview, so you don’t have to.
And here’s how you can answer it:
A cache is used to store frequently accessed data, thus serving future requests faster. Also it keeps data in memory for low latency. Yet the available memory is limited. So frequent updates to the cache are necessary.
The technique of storing, retrieving, and managing data in a cache for performance and optimal memory usage is called a cache strategy.
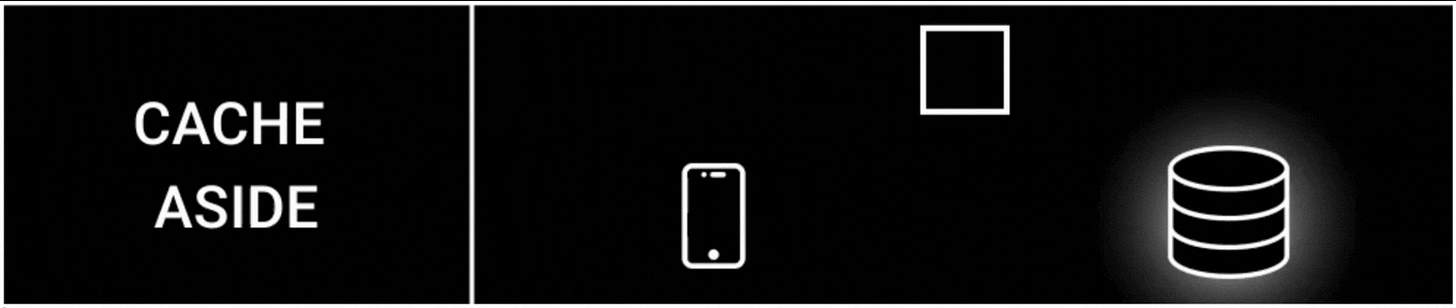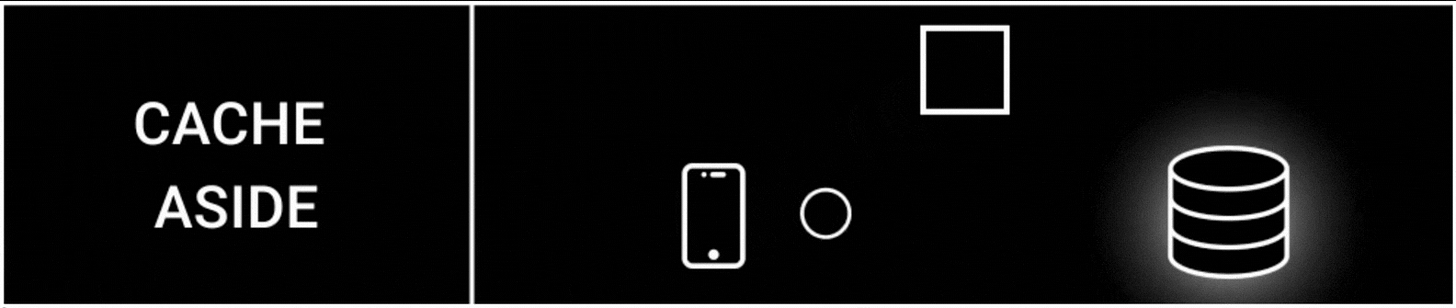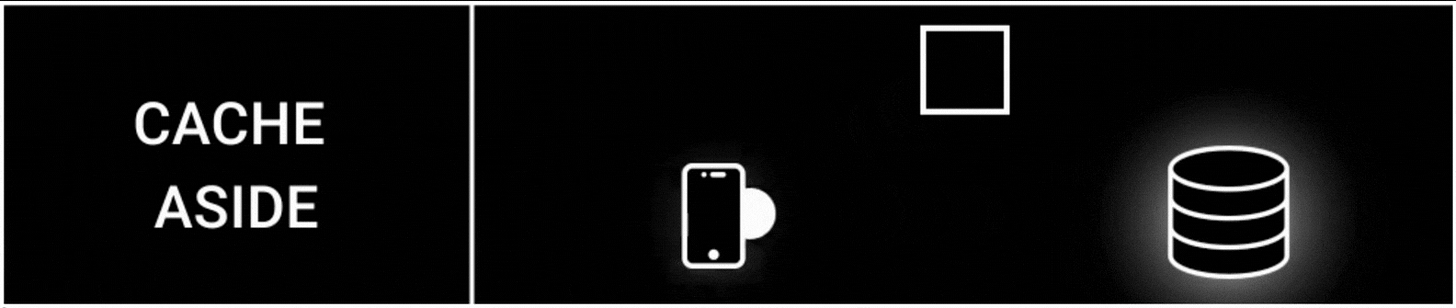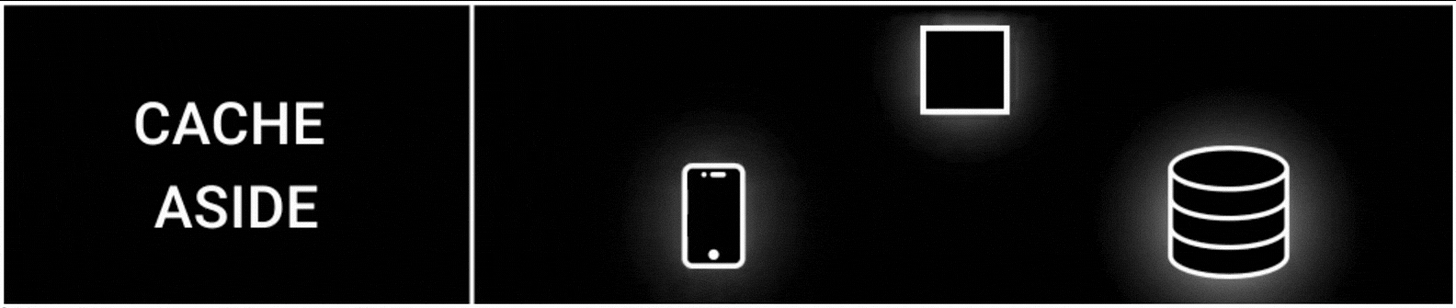
1. Cache Aside Strategy
The cache aside is one of the most popular cache strategies.
It’s also called lazy loading because data gets cached only when it’s queried.
Here’s how it works:
The app tries to read data from the cache
It then reads data from the database on a cache miss
The data gets written to the cache
A cache miss means the queried data is unavailable in the cache.
Besides the cache doesn't interact with the database directly; instead, the app does.
This strategy is easy to implement. But there’s a risk of data inconsistency and extra latency because of network round trips.
It’s used in read-heavy workloads, such as configuration data or user profiles.
Ready for the next technique?
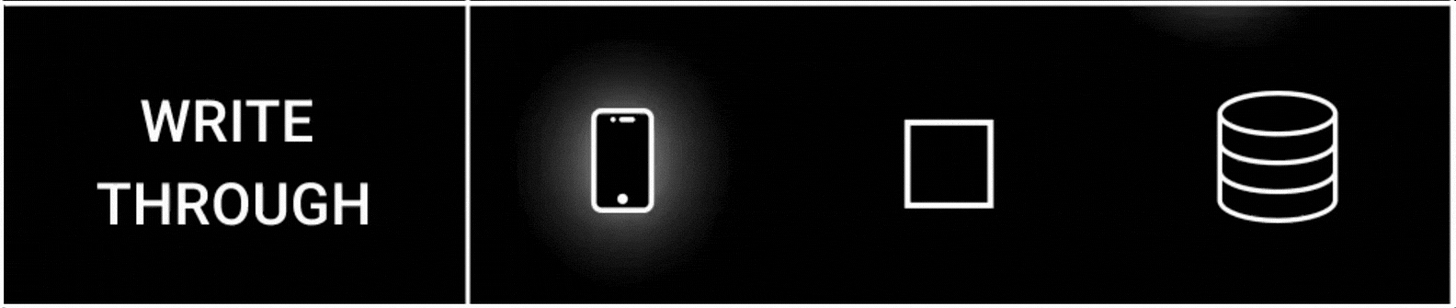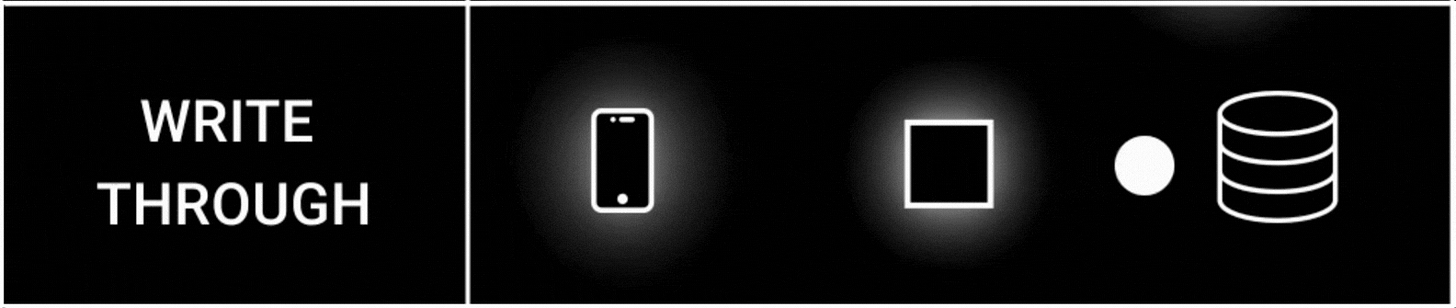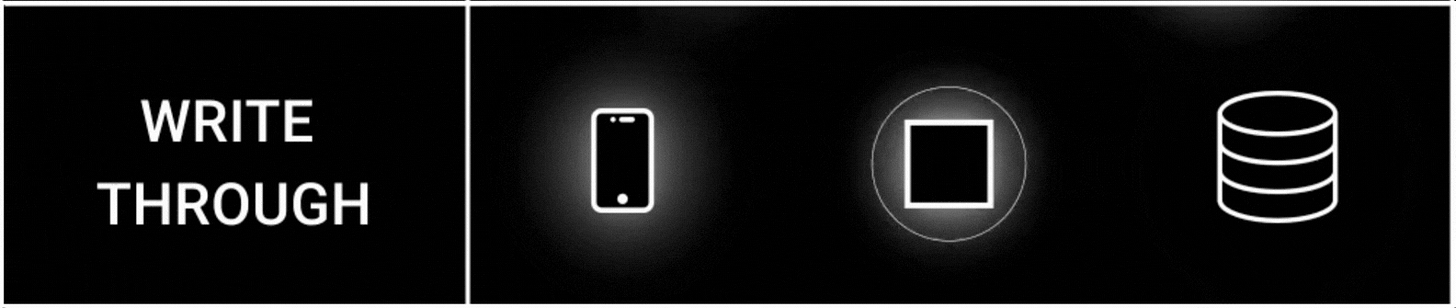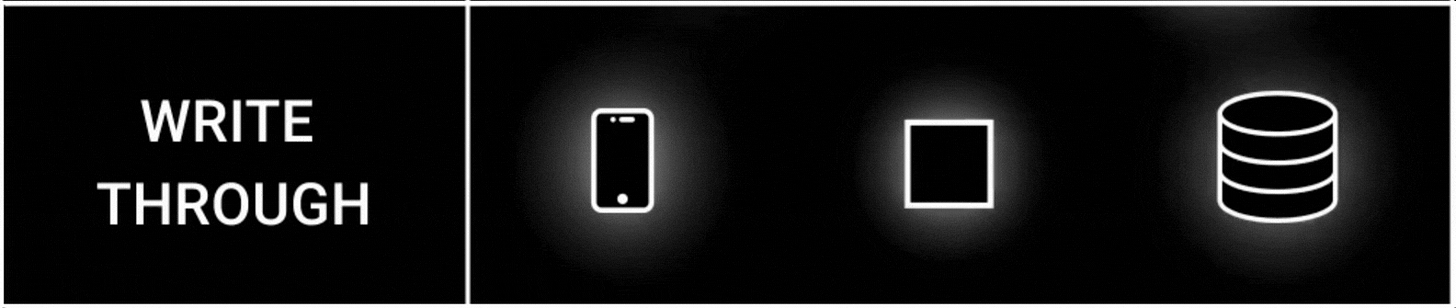
2. Write Through Strategy
The write-through cache strategy ensures strong consistency between the cache and the database.
Here’s how it works:
The app writes to the cache
The cache then writes to the database synchronously.
The app doesn't interact with the database directly; instead, the cache does.
Although this strategy offers data consistency, the latency on writes is higher. Also the cache space might get wasted with infrequently accessed data.
It’s used where write rate is low, and when data freshness is critical.
3. Read Through Strategy
The read-through cache strategy installs the cache between the app and the database. This means all reads go through the cache.
Here’s how it works:
The app reads data from the cache
Then it reads data from the database on a cache miss
The data gets written to the cache and then returned to the app
The app doesn't interact with the database directly; instead, the cache does.
Although this strategy offers low latency, there’s a risk of data inconsistency.
It’s used in read-heavy workloads, such as a newsfeed or a product catalog.
Let’s keep going!
4. Write Back Strategy
The write-back strategy writes data to the cache for batching and performance. This means write latency is low.
Here’s how it works:
The app writes to the cache directly
The cache then writes data to the database asynchronously
This strategy offers better write performance through batching. Yet there’s a risk of data loss if the cache fails before writing to the database.
It’s used in write-heavy workloads where throughput is more important than durability.
5. Write Around Strategy
Here’s how the write-around cache strategy works:
The app writes to the database
It tries to read data from the cache later
The app reads from the database on a cache miss
It then updates the cache
Although this strategy optimizes cache storage for frequently accessed data, there is a risk of increased latency because of cache misses.
It’s used for large data objects where updates happen rarely.
TL;DR:
The 2 popular cache implementations are Redis and Memcached.
Read heavy workload: use cache aside or read through strategies
Consistency vs throughput: use write-through or write-back strategies
Avoid caching one-off writes: use write-around strategy
It’s important to pick the right cache strategy based on your needs and tradeoffs.
Subscribe to get simplified case studies delivered straight to your inbox:
Want to advertise in this newsletter? 📰
If your company wants to reach a 150K+ tech audience, advertise with me.
Thank you for supporting this newsletter. Consider sharing this post with your friends and get rewards. Y’all are the best.
TL;DR 🕰️
You can find a summary of this article here. Consider a repost if you find it helpful.











congrats on 150k Neo! :)
Cache is probably the closest thing we have to a silver bullet.
But only if you're willing to aim it carefully, invalidation is still hard.
Good breakdown, Neo.